Authenticated Scan
Description
Authenticated Scan is a feature that facilitates security scanning of applications requiring authentication by leveraging cookies and forms. It is compatible with both monolith and microservice architectures, ensuring comprehensive coverage of protected application areas.
note
To use the authentication feature, users must first follow the scanning steps. After that, the user selects the Website Scanner tool because only the Website Scanner tool has the authentication feature. Then, activate the authentication feature by clicking Enabled Authentication, and the Session Cookies and Form will appear. Users can also choose to apply it to monolith or microservice services.
Steps Using Authenticated Scan
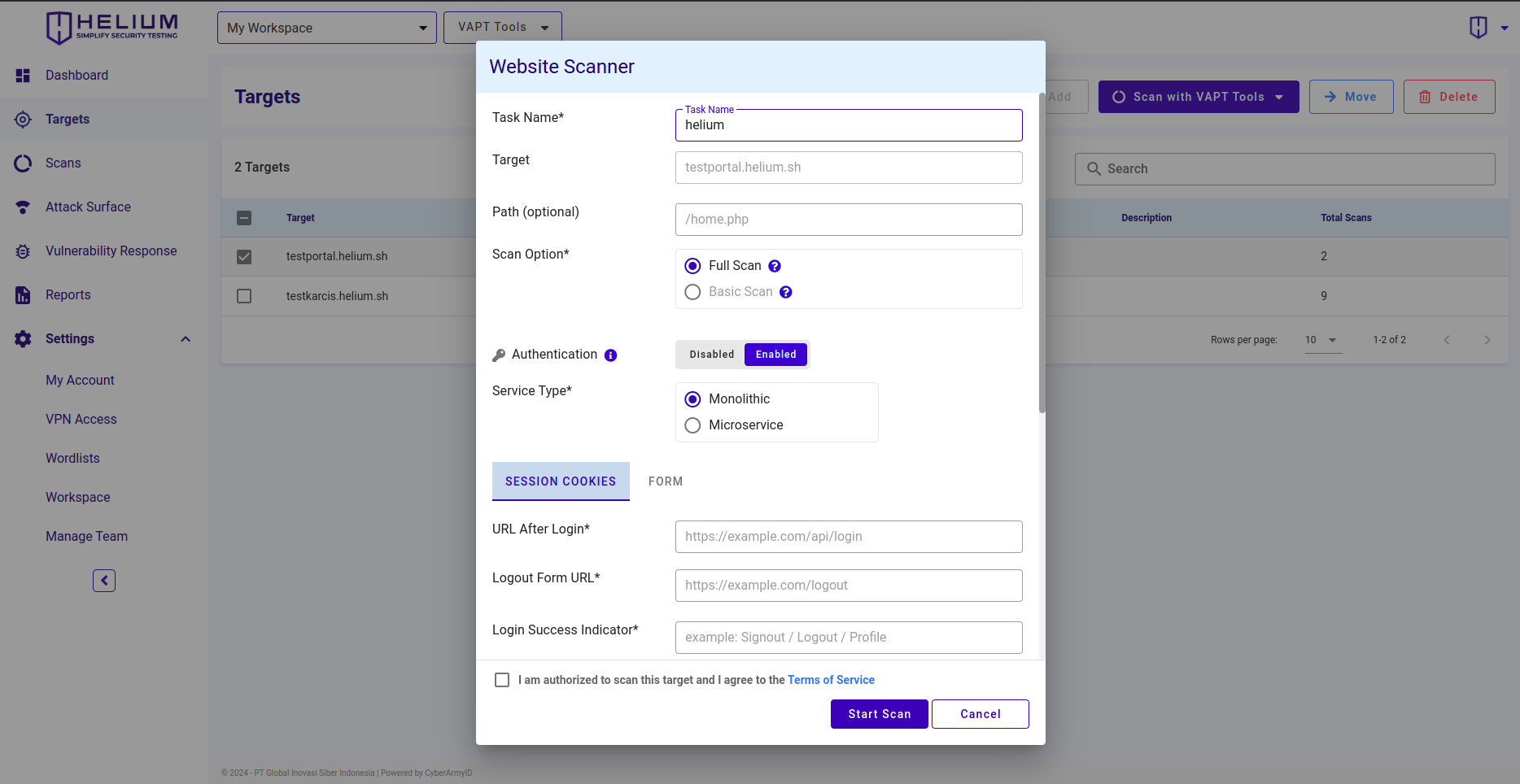
 Users can follow the following steps.
Users can follow the following steps.
- Choose the Service Type, Monolith or Microservice
- To fill in the Session Cookies, click the Session Cookie section and complete the form. Users can see the examples listed
- Enter URL After Login in the URL After Login textbox
- Enter Logout Form URL in the Logout Form URL textbox
- Enter Login Success Indicator in the Login Success Indicator textbox
- Enter Logout Success Indicator in the Logout Success Indicator textbox (optional)
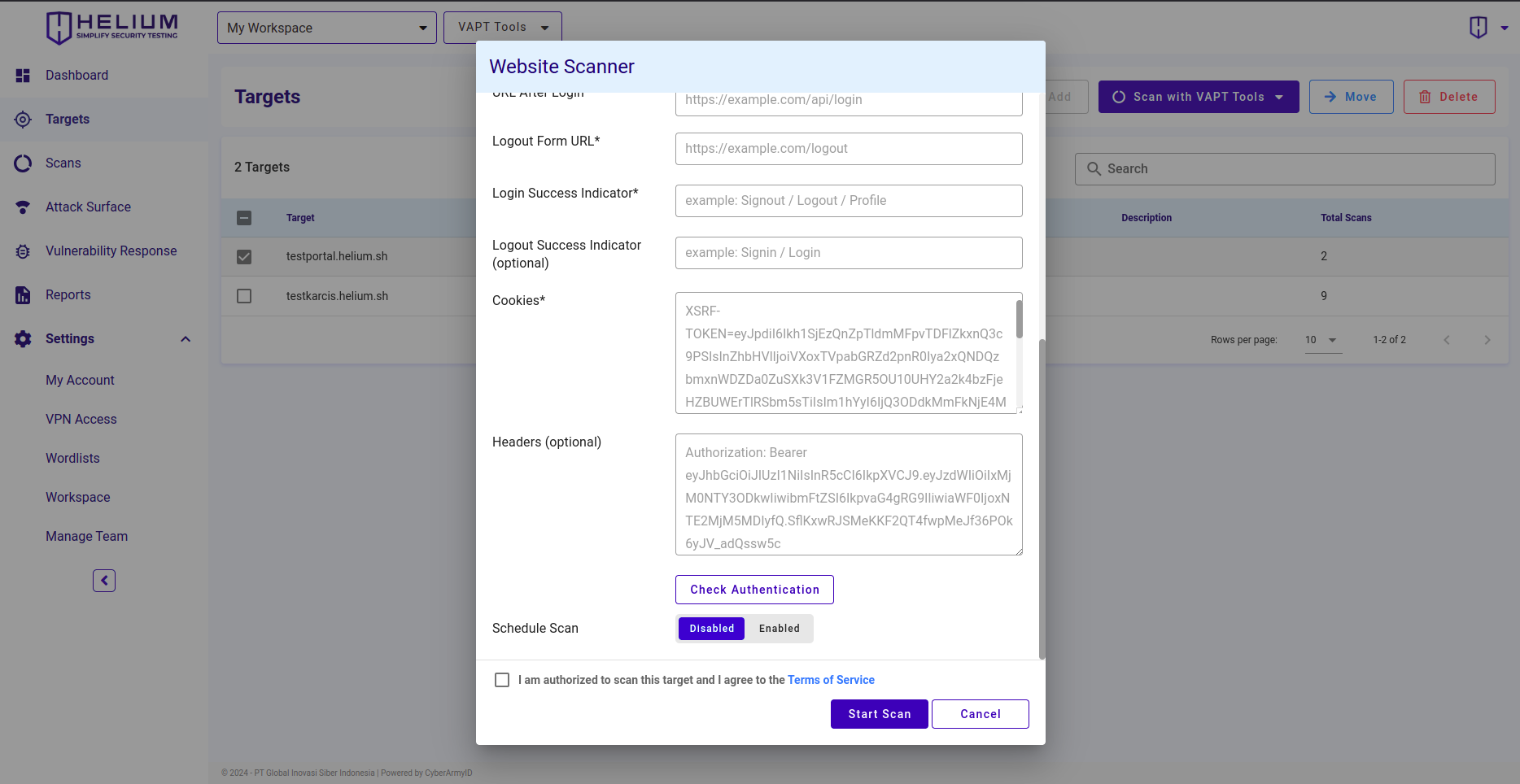
- Input cookies in the Cookies textbox
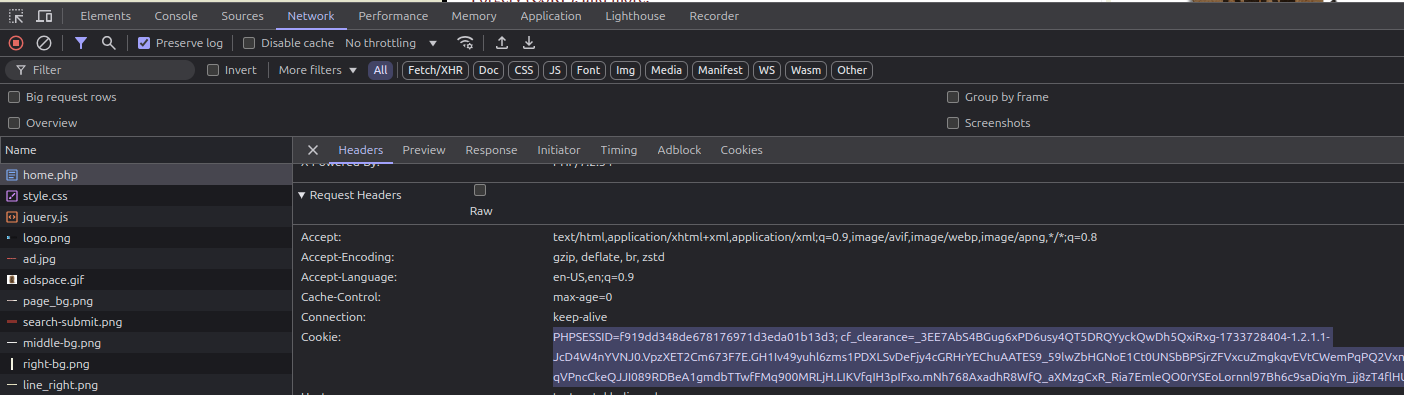
- Input header in the Header textbox (optional)
- To fill in the Form, click the Form section and complete the form. Users can see the examples listed
- Enter the login form URL in the Login Form URL textbox
- Enter the login page URL in the Login Page URL textbox (optional)
- Enter the login request payload in the Login Request Payload textbox
- Enter logout Form URL in the Logout Form URL textbox
- Enter login success indicator in the Login Success Indicator textbox
- Enter logout success indicator in the Logout Success Indicator textbox (optional)
- Input cookies in the Cookies textbox (See: Step 7)
- Input header in the Header textbox (optional)
- Click the Check Authentication button to ensure that the cookie used is valid for testing.
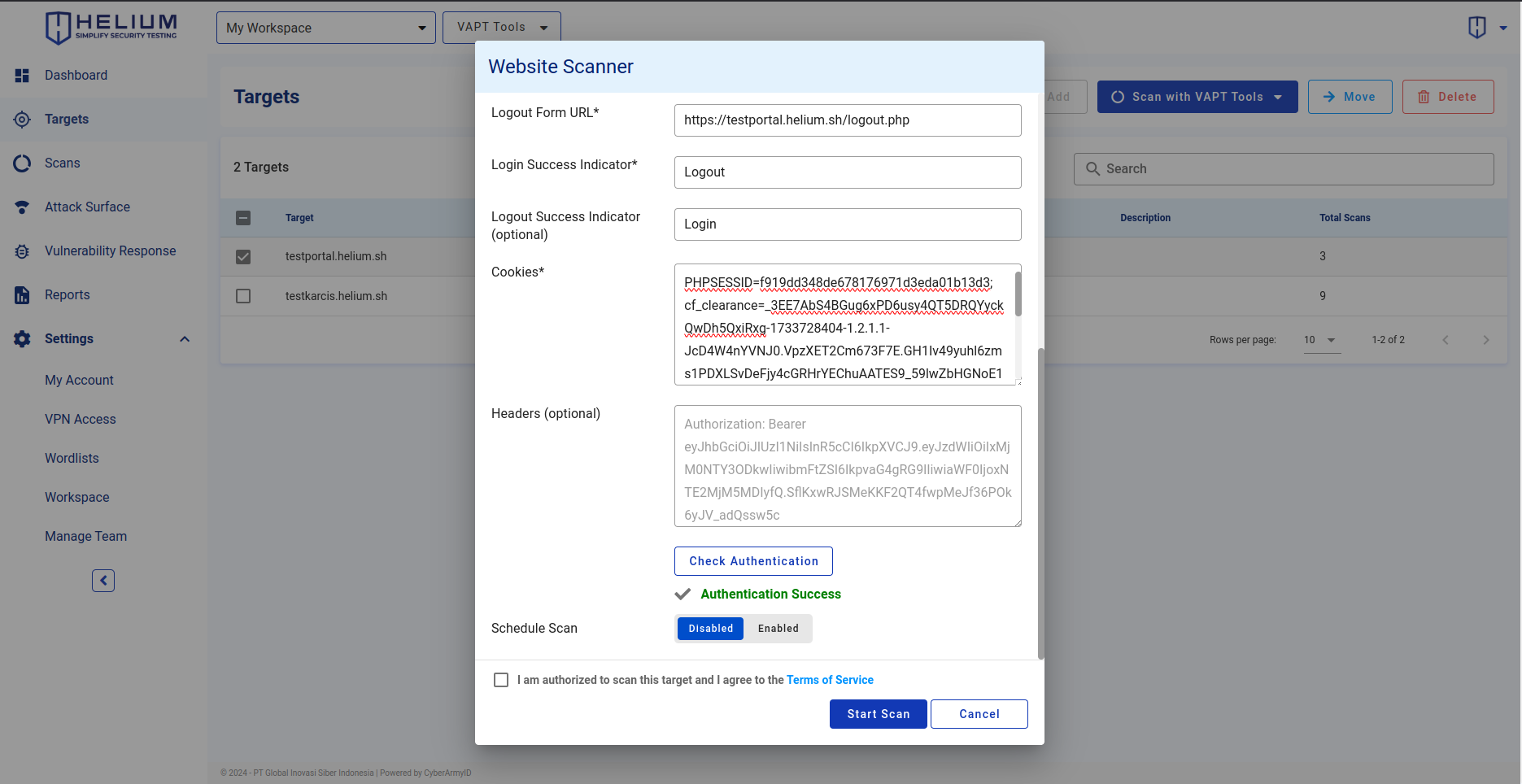
- If Authentication Success, click the agree Terms of Service checkbox
- Click the Start Scan button to start the scan, and click Cancel if you want to cancel