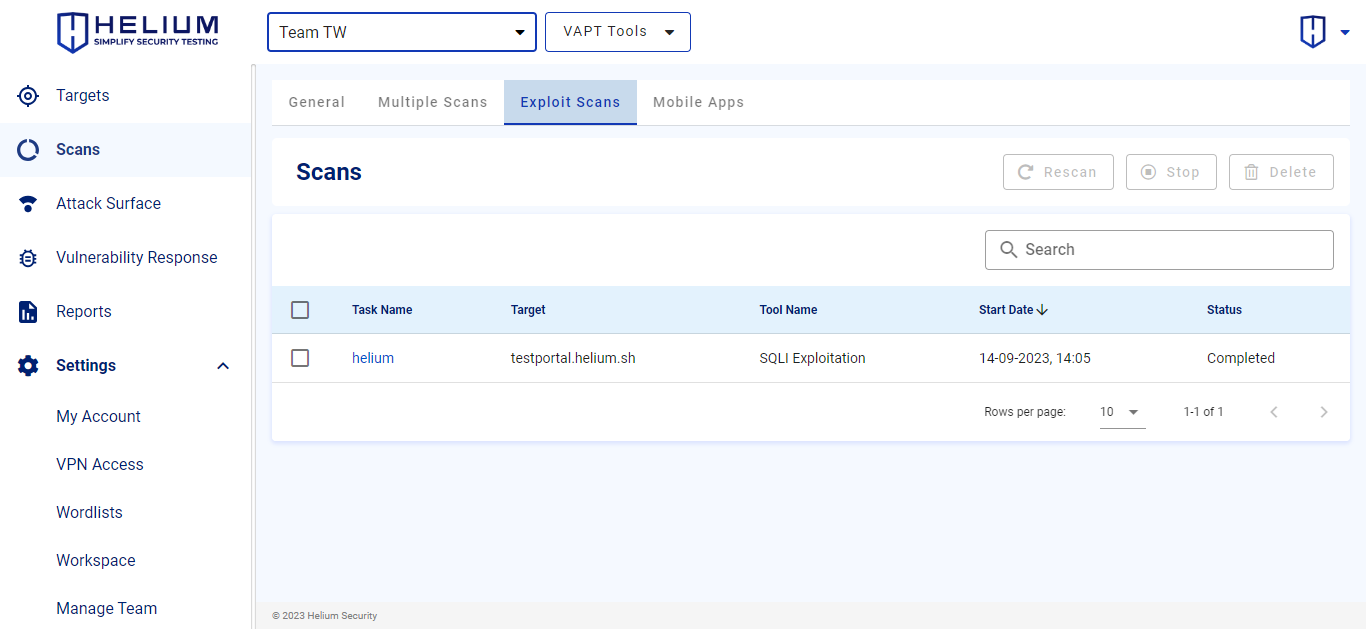
Exploit Scans
Description Exploit Scans
Users are able to take advantage of the scanning feature by selecting from various scan options such as Domain, Direct, and Request. Upon completion of the scan, users can view results in the form of logs or a database. However, this exploit scan feature will appear if you only use the SQLi Exploitation tool.
info
- Task Name is the name of the target being scanned
- Tool Name namely the tool used on the target
- Target is the target to be scanned in the form of a domain or IP
- Start Date is the time the target was scanned
- Status indicates the current condition of the target, and it is marked as Completed when the target has been successfully scanned
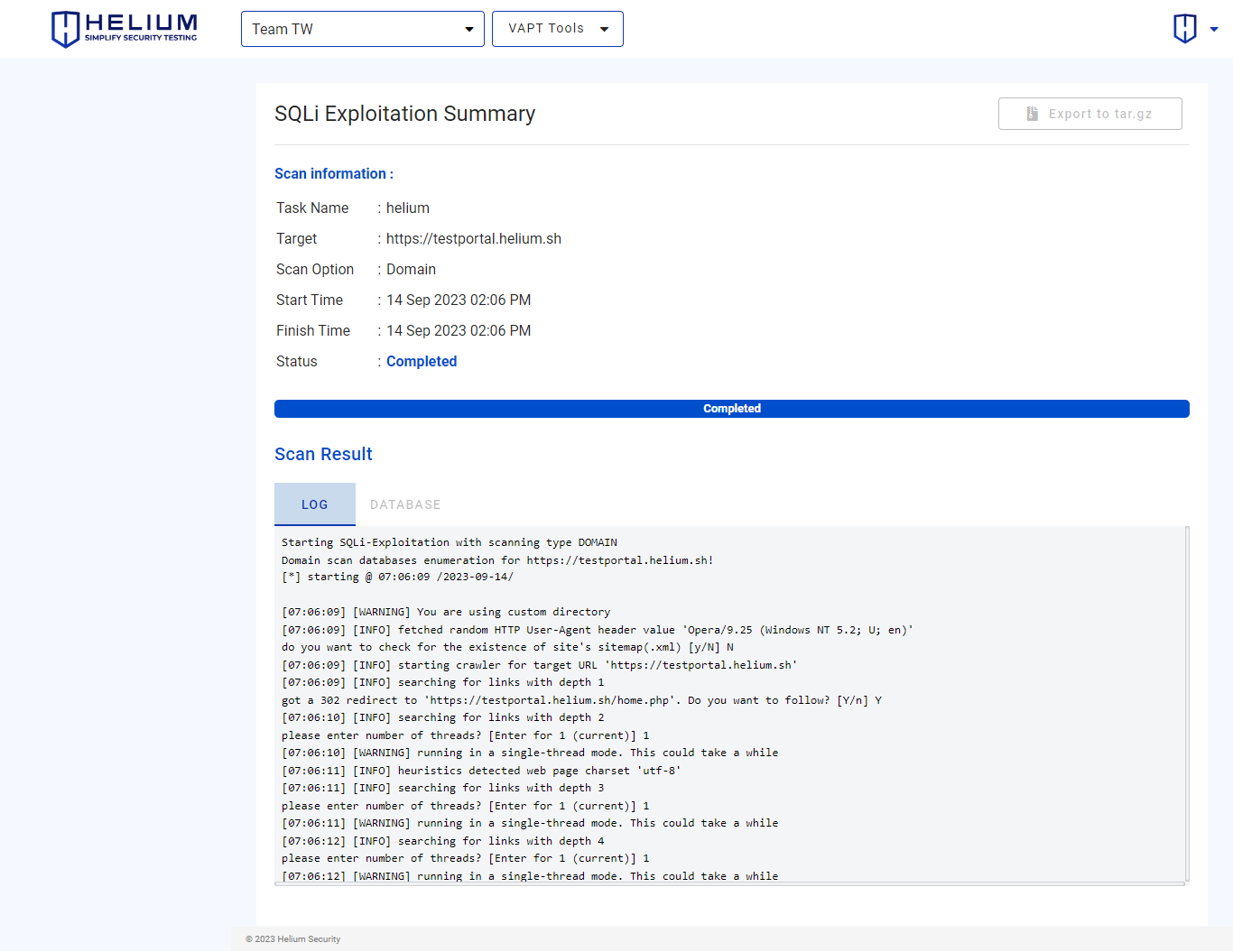
View SQLi Exploitation Summary
On the Exploit Scans page, users can see targets that use the exploit scan feature as follows.
 Users can click on the blue task (example: helium) and they will be directed to a summary results page of the scan, in the form of concise information as follows.
Users can click on the blue task (example: helium) and they will be directed to a summary results page of the scan, in the form of concise information as follows.