Plan Details
The Plan Details page displays information on the active license, license validity period, and features that can be accessed by users, as shown below.
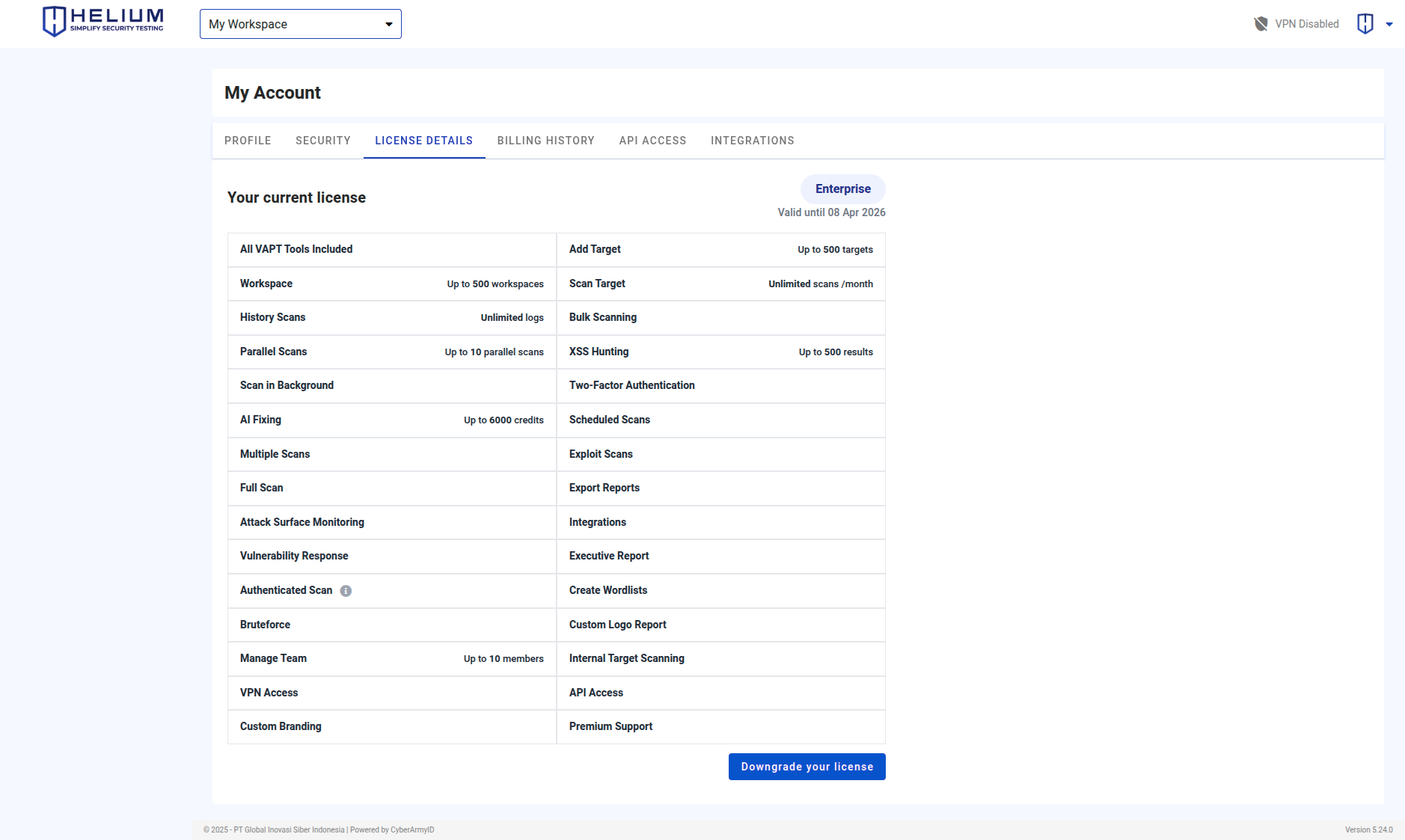
However, there are limitations to using these features. There are several types of user licenses, namely as follows:
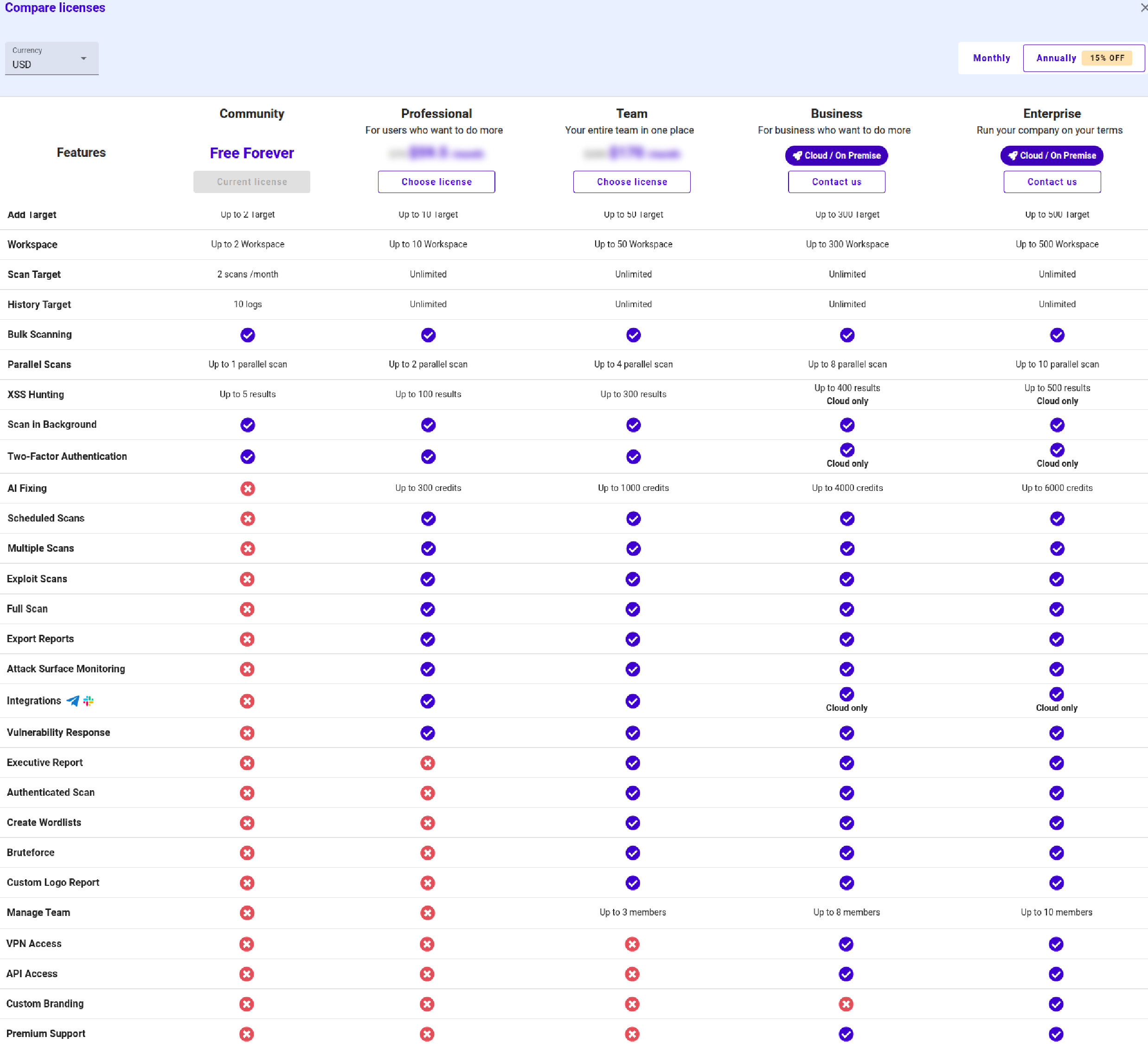
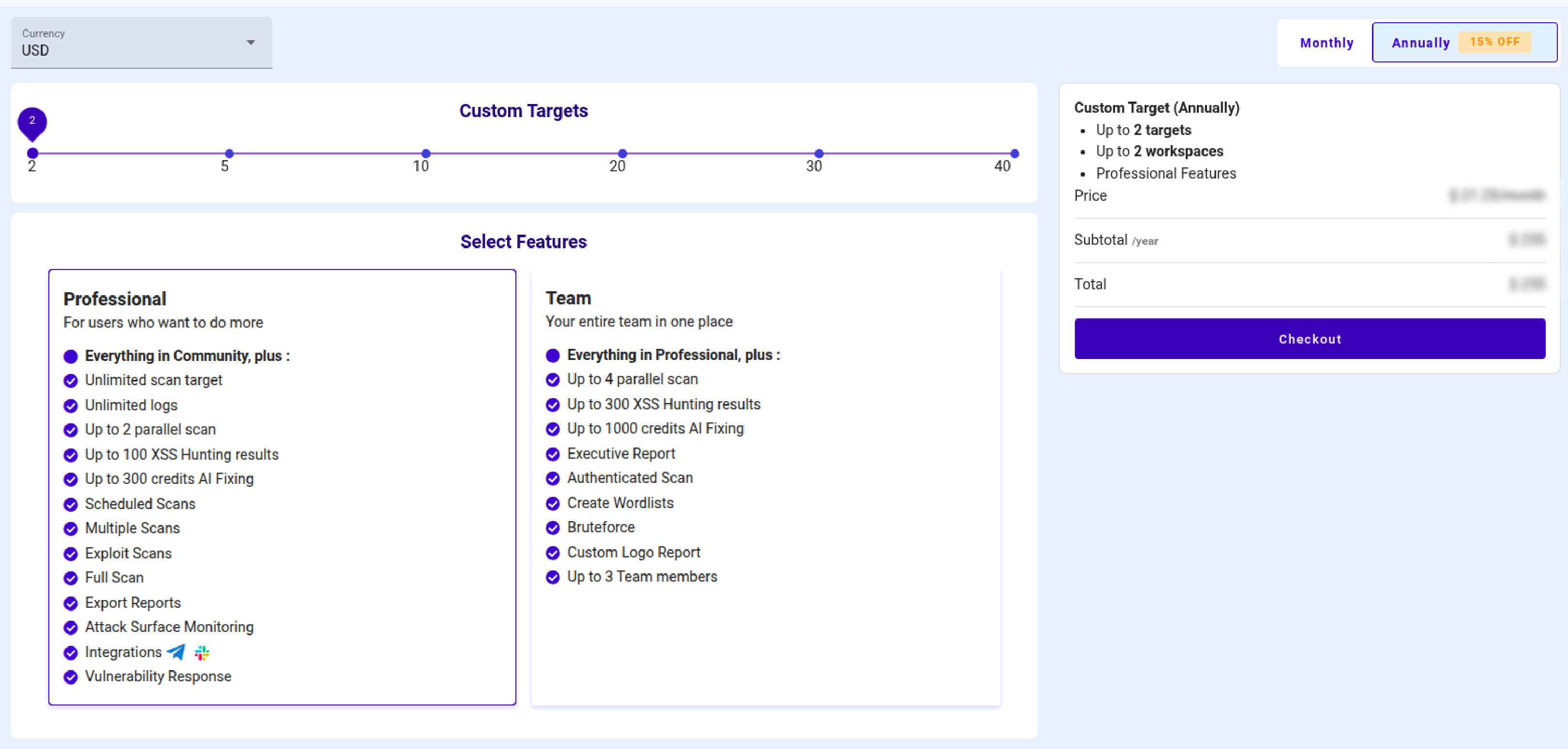
If you require a specific target quantity that aligns with your business needs, we also offer customized plans that can be fully tailored to match your organization’s goals and scale.
- Custom Targets (Professional Features): You can choose targets according to your needs with all the Professional features.
- Custom Targets (Team Features): You can choose targets according to your needs with all the Team features.
Features Available in Helium
- All VAPT Tools Included: Vulnerability Assessment and Penetration Testing (VAPT) is a range of security testing services to identify and address cybersecurity vulnerabilities.
- Add Target: Targets are the systems you run the scans against. They can be URLs, hostnames, and IPs. Users can add multiple targets via Import in Txt format.
- Workspace: A workspace is a dedicated environment where you can organize and manage your targets, scans, and results efficiently. It helps teams collaborate and keep projects separated for better workflow.
- Scan Target: The selected target will be scanned with the available tools.
- History Scans: Scans of history comprise records of the targets that have been scanned.
- Bulk Scanning: This feature allows the selection of multiple targets. It can then scan multiple targets simultaneously, but according to the user's license.
- Parallel Scans: A feature that can scan several targets simultaneously with the number of parallel scans according to the user license, namely for communities only 1, for professionals a maximum of 2, for teams a maximum of 4, and for enterprises a maximum of up to 10 parallel scans.
- XSS Hunting: Assuring your Proofs-of-Concept and demonstrating the risk of XSS vulnerabilities in web applications.
- Scan in background: A feature that allows users to continue scanning a target even while using other programs on their device.
- Two-Factor Authentication (2FA):: An extra security step when logging in. You enter your password and a code sent to your phone or generated by an app to keep your account safe.
- AI Fixing: AI Fixing helps provide recommendations for each finding, guiding you on how to address issues effectively.
- Schedule Scans: Users can set the target scanning schedule according to the time they want.
- Multiple Scan: This feature enables users to select multiple targets and apply 2 to 10 tool options per target, with results grouped by target.
- Exploit Scan: Users are able to take advantage of the scanning feature by selecting from various scan options such as Domain, Direct, and Request. Upon completion of the scan, users can view results in the form of logs or a database. However, this exploit scan feature will appear if you only use the SQLi Exploitation tool.
- Full Scan: The feature that performs comprehensive scanning is reading all the findings more deeply, starting from crawling, then scanning passively and also actively. Different from Basic Scan, basic scan only reads some of the findings.
- Export Reports: Scan report results can be exported into document format.
- Integrations: Can be integrated into both Telegram and Slack, with a bot feature that sends scan result notifications directly to Telegram. Users can also scan via Telegram and Slack bots.
- Vulnerability Response: This feature displays scanned targets along with their vulnerability information. However, users can only see vulnerability response information if they use the VA Scanner tool (Website Scanner, API Scanner, Network Scanner).
- Executive Report: A summary report that presents key findings and insights in a clear and easy-to-understand format, designed for managers and decision-makers.
- Authenticated Scan: A feature that allows users to scan login credentials by providing cookies and forms.
- Create Wordlists: Can create Wordlists, these Wordlists are used in various tools such as Bruteforce and Find Website Directory
- Bruteforce: With this Bruteforce feature, it is possible to test passwords, login credentials or even encryption keys automatically by trying various possible combinations until finding the correct login information.
- White Label Reports: A feature that allows changing the logo on the report document cover so that users can change the logo according to their wishes.
- Manage Team: Collaborate with the team to enhance security assessments and view the team activity log.
- VPN Access: VPN Access allows users to scan targets within the user's internal network.
- API Access: The API allows you to integrate our platform with your tools and internal workflows. For instance, you can trigger automatic scans whenever you deploy a new website, or you make a change in your application. Furthermore, you can develop your tools based on our scanning engines.
- Custom Branding: Users can upload their organization’s logo to appear on the Helium dashboard and also add a logo for emails.
- Premium Support: This feature is only available for enterprise user licenses. Users will be given priority assistance, which can include users getting priority access to technical support, 24/7 support, faster troubleshooting, additional security controls, and much more.